Virtual Machine Security
Ensuring Virtual Machine Security in Cloud Computing
Introduction
A VM or Virtual Machine is a way to create a computer within a computer so that you can run different operating systems on the same machine. So, for example if your computer works on Windows, with a VM, you could also run Linux on the same machine. Virtual machines are basically computer files that behave like actual computers. The software in a virtual machine doesn’t escape or tamper with that of the actual computer, therefore the reason why it runs in a separate window. Multiple virtual machines can run simultaneously at the same time on the same computer, too.
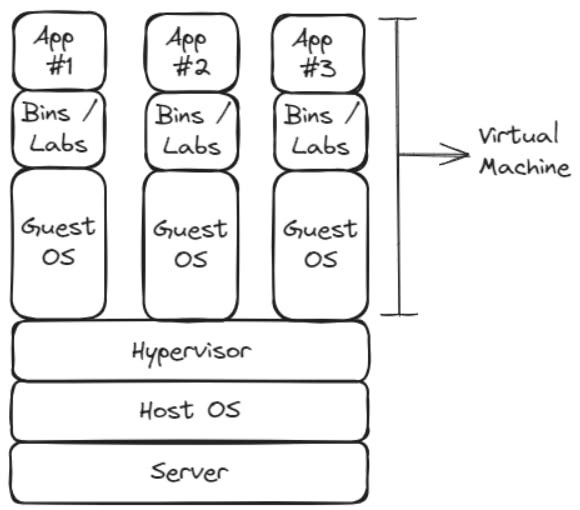
Virtualization technology allows us to virtualize computer systems and eliminate many drawbacks surrounding traditional IT setups. As businesses are increasingly open to cloud computing and virtualization, providing security virtual machines becomes a top priority.
But how can organizations ensure VM security in cloud computing?
Virtual machine security or virtualized security refers to a series of security solutions that use software to protect virtual systems and environments instead of hardware. The difference between virtualized security and hardware-based security is flexibility. Hardware-based security is tied to a device, such as a router, firewall, or switch, whereas software-based security can operate anywhere in the network. With virtualization technology, we add another layer of security (virtualization layer) to virtual machines.
Benefits of Virtual Machine Security?
Now there will be a question — why should organizations turn to cloud computing and virtual systems as replacements for traditional infrastructures? Virtual networks are becoming more and more demanding and no aspect of virtualization is more demanding than security. Nowadays, there are many ways how a threat actor can breach your virtual infrastructure and compromise security controls. Hence, It’s crucial to protect virtualized security in cloud computing technologies such as isolating multitenant setups in public cloud settings. Because data and workloads move around a complex ecosystem including several providers, virtualized security’s flexibility is useful for securing hybrid and multi-cloud settings.
Flexibility
As long as we’re still operating in the same virtual environment, we can shift workloads and protect our data across multiple VMs, data centers, and hybrid deployments. Virtualization security through software allows us to manage data security policies on individual virtual machines.
Cost-Efficiency
Each guest operating system in a virtualized environment gets access to resources from a pool. But virtualized security also benefits from cost efficiency as it allows organizations to maintain a secure network without needing to pay over the top for security hardware. Virtual machines have one inherent benefit that traditional environments don’t — they’re less costly to deploy.
Operational Efficiency
Another benefit of virtualized security is operational efficiency. Modern workloads focus on hasty deployments. Unfortunately, physical security involves a series of steps that take much longer to implement than virtual machine security. In addition, installing the latest security patches can be a hassle, and it will most likely require IT teams to go over the operational configurations. On the other hand, virtualization security works through a management platform where the software does everything. In addition, virtualization security allows for rapid deployment, automation, and also the scalability of security software.
Faster Deployment
Modern hypervisors will allow you to deploy new VMs in minutes. If you’re using a VM template, the time to deploy new instances will be reduced even more.
Security Features of VM
Virtual Machine Shields
Virtual machine shields or VM shields or Shielded VM is a popular virtualized security feature that offers verifiiable integrity to our Compute Engine VM instances, so we can be confident that the instances haven't been compromised by boot or kernel-level malware or roorkits. It uses encryption at the virtual hard-disk level to prevent unauthorized tinkering of VMs. Each virtual machine gets its own encryption key, meaning only a dedicated and authorized host can access the VM. What this feature tells us is that no threat actor can start, shut down, migrate, or delete a virtual machine if they don’t have the encryption key.
Role-Based Access Control
Another popular virtual machine security feature is Azure Role-Based Access Control (Azure RBAC). It is an authorization system built on Azure Resource Manager that provides fine-grained access management to the Azure resources. The way you control access to these resources using Azure RBAC is to assign Azure roles. A role is a collection of permissions. It lists the actions that can be performed, such as read, write and delete. Roles can be high-level like owner or specific, like virtual machine reader.
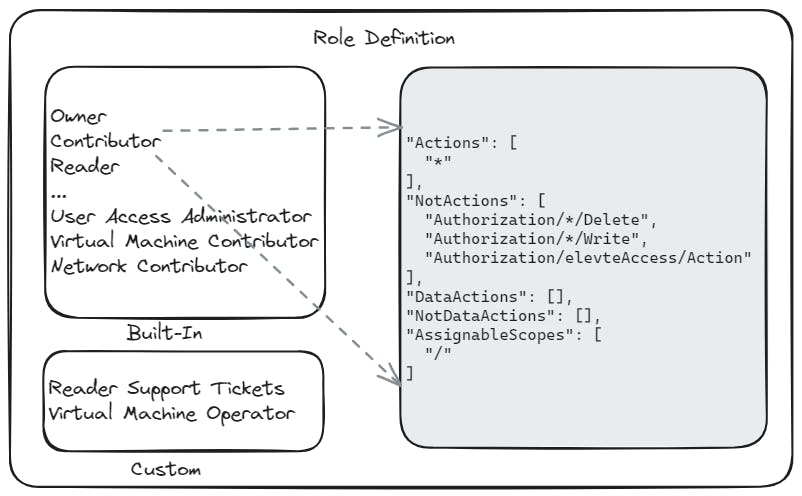
RBAC limits the number of permissions an administrator is assigned. The feature will see more success in larger organizations where file sharing on guest operating systems is more common.
Some examples of RBAC roles:
Owner: The owner role grants full access to all resources within a subscription. This role allows users to create, delete, and modify all resources.
Contributor: The contributor role allows users to create and manage resources, but they cannot grant access to others or delete resources they did not create.
Reader: The reader role allows users to view resources but does not allow any changes to be made to them.
User Access Administrator: This role allows users to manage access to resources for other users.
Virtual Machine Contributor: The virtual machine contributor role allows users to create and manage virtual machines.
Network Contributor: The network contributor role allows users to create and manage network resources such as virtual networks, subnets, and network security groups.
Storage Account Contributor: The storage account contributor role allows users to create and manage storage accounts.
Sandboxing
Sandboxing can be performed using different techniques and tools. Virtual Machines are commonly used for sandboxing purposes. A VM allows analysts to create an isolated operating system environment within their host machine. Any changes made by the malware within the VM can be easily discarded, ensuring the host system’s safety. Other sandboxing techniques include containerization, which provides lightweight virtualization, and dynamic analysis tools that offer sandbox-like environments for malware execution and monitoring.
- Isolation and Security: Sandboxes offer a secure environment by containing malware within a virtual machine or a container, preventing it from infecting the host system and spreading to the network.
- Behavior Analysis: Sandboxing enables analysts to observe the actions and behavior of malware, such as network communications, file modifications, and system interactions. This insight helps in identifying the purpose and potential impact of the malware.
- Payload Analysis: By executing malware in a sandbox, analysts can study the payload and any potential actions it may perform, such as data exfiltration, system compromise, or launching further attacks.
- Dynamic Analysis: Sandboxing allows for real-time monitoring of malware activities, capturing system calls, API interactions, and network traffic. This dynamic analysis aids in understanding the malware’s runtime behavior.
Security Through Segregation
A common “best practice” for virtual machine security in cloud computing is to isolate virtual machines from the physical host hardware system. In a virtualized environment, the solutions are software-based. Therefore, we can isolate or segregate VMware virtual machines and their hosts by isolating the hosting and connections inside a private subnetwork.
Conclusion
Virtual systems are more secure than physical systems, and the testing of such software is a big part of virtualization. After all, we use virtual machines mostly for testing software, applications, and operating systems. Virtualization security must not become an afterthought after the new virtual infrastructure and components are put into place. Security in this area will improve as virtualization technology advances, and standards will need to be put into place so that firms have guidelines to follow to secure their new environments.
